
Struggling to keep up with the growing number of threats? Managed vulnerability management can be your answer. It’s outsourcing the task of identifying, assessing and mitigating vulnerabilities to expert providers so your business stays protected without having to build an in-house team.
This article will walk you through the benefits and core functions so you can decide if it’s right for your business.

Managed vulnerability management is outsourcing the entire vulnerability lifecycle to third party providers so businesses without specialist staff can manage vulnerabilities without having to build an in-house team. These services provide a structured approach to managing the lifecycle of vulnerabilities so security weaknesses are systematically identified and fixed. Vulnerability management is crucial in today’s threat landscape where new vulnerabilities emerge daily and the stakes are higher than ever.
Vulnerability management services scan systems, analyse results and help fix issues making them an essential part of a comprehensive cybersecurity strategy. These services are especially important for businesses that don’t have the resources or expertise to manage vulnerabilities themselves. By using managed vulnerability management businesses can continuously improve their security posture and address critical vulnerabilities quickly.
The core functions of managed vulnerability management services provide a holistic approach to identifying and addressing vulnerabilities. This includes:
Ongoing monitoring in managed vulnerability management verifies remediation efforts and identifies new vulnerabilities. The processes managed by vulnerability experts include scan operations, threat intelligence gathering and vulnerability validation all of which improve the overall security posture of an organisation.
Effective tools provided by trusted providers should offer automated scanning, custom reporting and integration with existing security systems.
The increasing average ransom demanded by attackers highlights the need for managed vulnerability services. As the threat landscape evolves, outsourcing vulnerability management becomes more beneficial:
Outsourcing vulnerability management also helps organisations meet increasing compliance requirements which can be a big task for internal teams. Partnering with managed vulnerability management experts reduces risk exposure and addresses vulnerabilities quickly and effectively. This proactive approach to security is essential in today’s fast paced digital world.
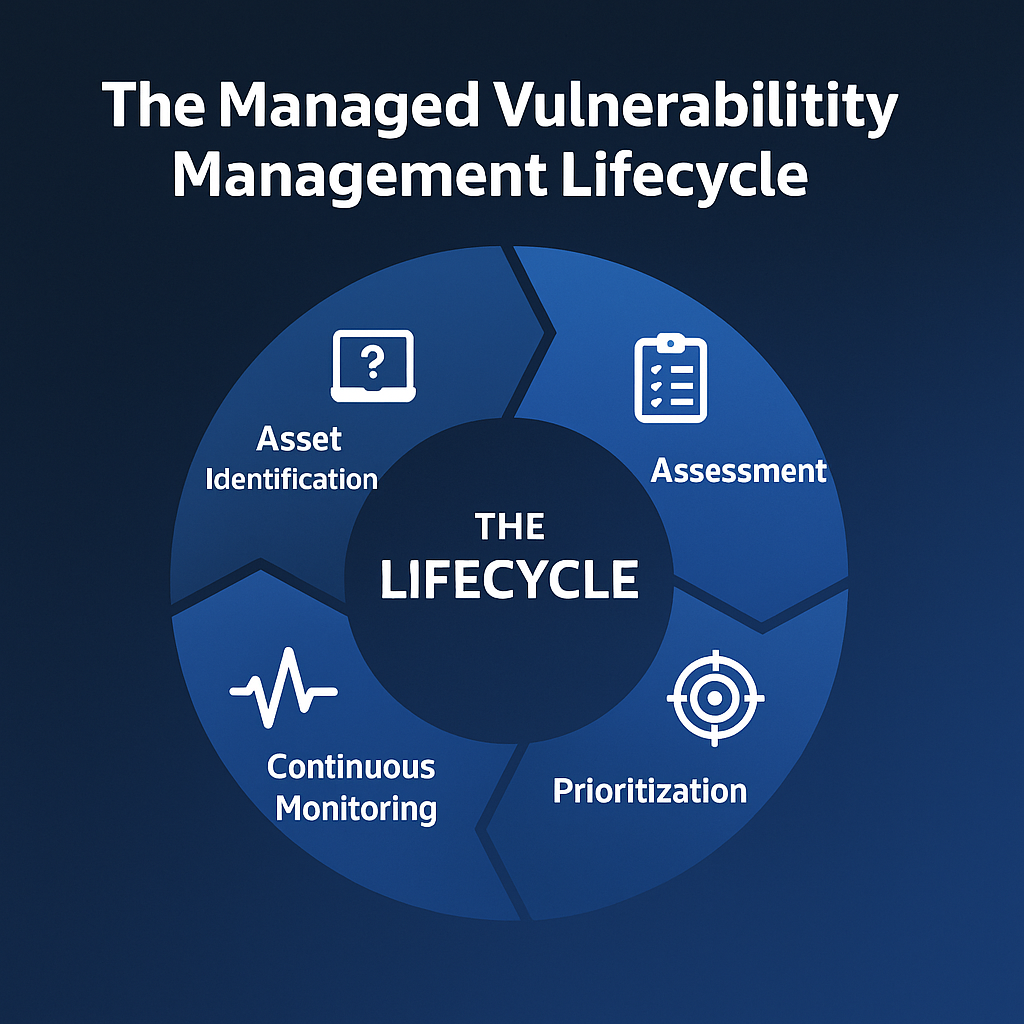
The managed vulnerability management lifecycle is a structured process that includes several stages to manage and reduce vulnerabilities. These stages are:
Each stage plays a key role in an organisation’s security posture and enables proactive measures against potential threats.
Continuous improvement within the lifecycle means vulnerability management processes evolve with emerging threats and changing business needs. Understanding and implementing each stage means a robust proactive vulnerability management programme that can address the ever changing cyber threat landscape.
The first stage of the vulnerability management lifecycle is creating an asset inventory which is a list of all hardware and software within a network. This comprehensive inventory is essential for operations and helps security teams identify vulnerabilities across all assets. To assess these assets for vulnerabilities organisations often use automated vulnerability scanners and manual testing. Scanning regularly helps organisations identify new vulnerabilities as they emerge.
Regular vulnerability scanning helps identify not only existing vulnerabilities but also newly discovered threats that affect the organisation. This ongoing assessment is crucial for determining asset risk, exposure to vulnerabilities and prioritising issues based on impact.
Managed vulnerability management services identify, evaluate and mitigate risks associated with vulnerabilities so a proactive approach to security management.
Risk prioritisation is a key part of vulnerability management using frameworks like CVSS to categorise vulnerabilities based on severity. Vulnerability prioritisation involves assessing factors such as criticality ratings and impact to address the most critical vulnerabilities first. Focusing on the most critical threats means organisations can allocate resources effectively, optimise their security efforts and consider the risk level.Organisations should have a structured approach to vulnerability management that includes regular assessments, prioritisation of vulnerabilities and proactive remediation. After remediation has taken place it’s essential to re-assess the system to confirm the fixes worked as expected. This structured approach means high risk vulnerabilities that could cause damage to organisational assets are addressed quickly.
Continuous improvement and monitoring are key to a successful vulnerability management programme. Managed services provide actionable intelligence that helps identify and remediate vulnerabilities. Regular updates and discussions between managed service providers and in-house security teams are crucial to adapt to emerging threats. Understanding the immediate security risk and next steps for remediation is key to the overall vulnerability management programme.
The vulnerability management cycle runs continuously as new vulnerabilities emerge, requiring regular scans and updates to stay ahead of potential threats. The overall programme measures continual improvements to ensure effectiveness, adapt to new challenges and improve the organisation’s security posture over time. This proactive approach means the organisation remains resilient to emerging cyber threats.

Outsourcing vulnerability management offers many benefits:
Another big benefit is access to security experts who can respond to potential threats quickly and effectively. These experts bring special knowledge and experience that may not be in-house, so vulnerabilities are addressed quickly and effectively. Outsourcing allows organisations to leverage this expertise, improve their overall security posture and stay ahead of emerging threats.
Outsourcing vulnerability management can reduce accountability for vulnerability management, shifting the responsibility to specialist service providers. This means organisations can manage costs better, they don’t need to invest in building and maintaining an in-house team of vulnerability experts. Instead internal teams can focus on core business objectives, leading to better resource allocation and overall efficiency.
Keeping open communication channels between managed service providers and internal security teams speeds up the response to vulnerabilities. Working closely with specialist providers means organisations can address vulnerabilities quickly and continually improve their security posture.
This collaborative approach means the organisation can defend against cyber threats.
Using managed services can help organisations overcome the talent shortage in cybersecurity by providing access to trained professionals. When choosing a vendor for managed vulnerability management, consider:
Case studies can show how a provider has dealt with specific vulnerabilities for similar organisations. Customer feedback and case studies can inform the decision making process around the effectiveness of a managed vulnerability management provider. Keeping open communication channels between service providers and internal teams builds trust and security culture.
Using managed services helps organisations identify non-compliance issues that may be missed by standard vulnerability scanning tools. False positives can lead to alert fatigue, reducing the effectiveness of security teams and increasing the risk of missing real threats. Managed vulnerability services provide expert guidance in risk management so vulnerabilities are accurately identified and remediated.
Partnering with managed vulnerability management experts reduces overall risk exposure and compliance to regulatory requirements. These services provide remediation guidance aligned to industry standards so organisations can mitigate cyber risk and avoid regulatory fines.
By using managed services organisations can enhance their compliance and risk management efforts and have a more secure and resilient fully managed service security posture.
Organisations face many challenges in constantly identifying and remediating vulnerabilities. The complexity of IT infrastructures makes it harder to detect vulnerabilities across multiple systems and devices. Rapid technological changes add to the difficulty in identifying vulnerabilities. Outsourcing vulnerability management services can help an organisation’s cybersecurity by providing continuous visibility of system vulnerabilities.
Managed vulnerability management services address organisational challenges such as false positives and skills shortages. They can address critical vulnerabilities quickly. They have pre-built scripts for common issues. Using managed services helps organisations overcome these challenges and have effective and efficient vulnerability management processes.
False positives are a common challenge in vulnerability scanning often caused by outdated definitions, inaccurate asset inventories and misconfigured scanners. Over reliance on automated tools without human oversight can exacerbate this issue and increase false positives. A risk based approach helps prioritise vulnerabilities based on the real threat to the organisation so reduces the noise from false positives.Regularly updating scanning methodologies and threat intelligence can further reduce false positives. Continuous monitoring and improvement of vulnerability management processes is key to ensuring ongoing accuracy and relevance of vulnerability data. Addressing false positives means security teams can focus on real threats and overall risk management.
Organisations face a significant shortage of cybersecurity professionals which can delay vulnerability remediation. Many businesses are looking to talent from diverse educational backgrounds to fill these roles.
Managed vulnerability management services can help close this skills gap by providing access to experienced professionals who can offer expert guidance and support in resolving critical issues across various environments through patch management.
A proactive approach to vulnerability management can significantly improve an organisation’s security posture. This means continuous monitoring, regular vulnerability scanning and threat intelligence to stay ahead of emerging cyber threats. Identifying and remediating vulnerabilities quickly reduces the attack surface and mitigates the risk of exploitation by attackers.
Collaboration between managed vulnerability services and internal security teams is key to maintaining a robust security posture. Security operations should prioritise critical assets and ensure resources are allocated to the most critical threats.
Continuous improvement and proactive vulnerability management enhances overall security and resilience to cyber threats.

Best practices in managed vulnerability management is key to efficient operations and better risk management. A proactive vulnerability management strategy can improve an organisation’s overall defence against cyber threats. Continuous vulnerability management helps organisations stay ahead of newly discovered vulnerabilities and zero-day threats.
Regular vulnerability assessments and updates are essential to an organisation’s ability to defend against cyber threats. Regular employee training and awareness programmes are also key to an organisation’s defence against security threats.
Following best practices improves vulnerability management and the environment is more secure.
Scheduled vulnerability scans are critical to identifying new vulnerabilities that can exploit system weaknesses and compromise security. Not all vulnerabilities can be detected by basic scanning techniques so refining these techniques by adding contextual information can reduce false positives in vulnerability assessments.
Advanced analytics and machine learning can also detect the gap between true vulnerabilities and exploitable vulnerabilities during scans and enhance the accuracy of the assessments and remediate identified vulnerabilities.These advancements mean organisations can address real vulnerabilities faster, overall security posture improves. Regular scans are key to continuous monitoring and staying ahead of new vulnerabilities including pci dss and organisations should scan for potential threats regularly. Better detection algorithms reduces false positives so organisations can focus on real threats.
Risk based remediation planning is critical to managing vulnerabilities and prioritising resources based on impact. Focusing on the most critical vulnerabilities minimises the discovery to remediation timeframe and improves security posture, addressing the biggest risk. A remediation plan is required for this.
Better prioritisation of remediation efforts means resources are allocated where they are needed most, reducing overall risk exposure.
Continuous communication between managed service provider and internal security teams is key to ensuring vulnerabilities are addressed and understood. Open communication allows sharing of insights and updates on emerging threats which is critical for proactive vulnerability management. Continuous communication fosters a culture of improvement so internal teams can provide feedback and adjust strategies based on real-time data and experiences.
Collaboration between the managed service provider and internal security teams strengthens the overall security posture by aligning priorities and responding to vulnerabilities. This collaborative approach means the organisation’s security operations are well coordinated and vulnerabilities are addressed quickly and effectively.
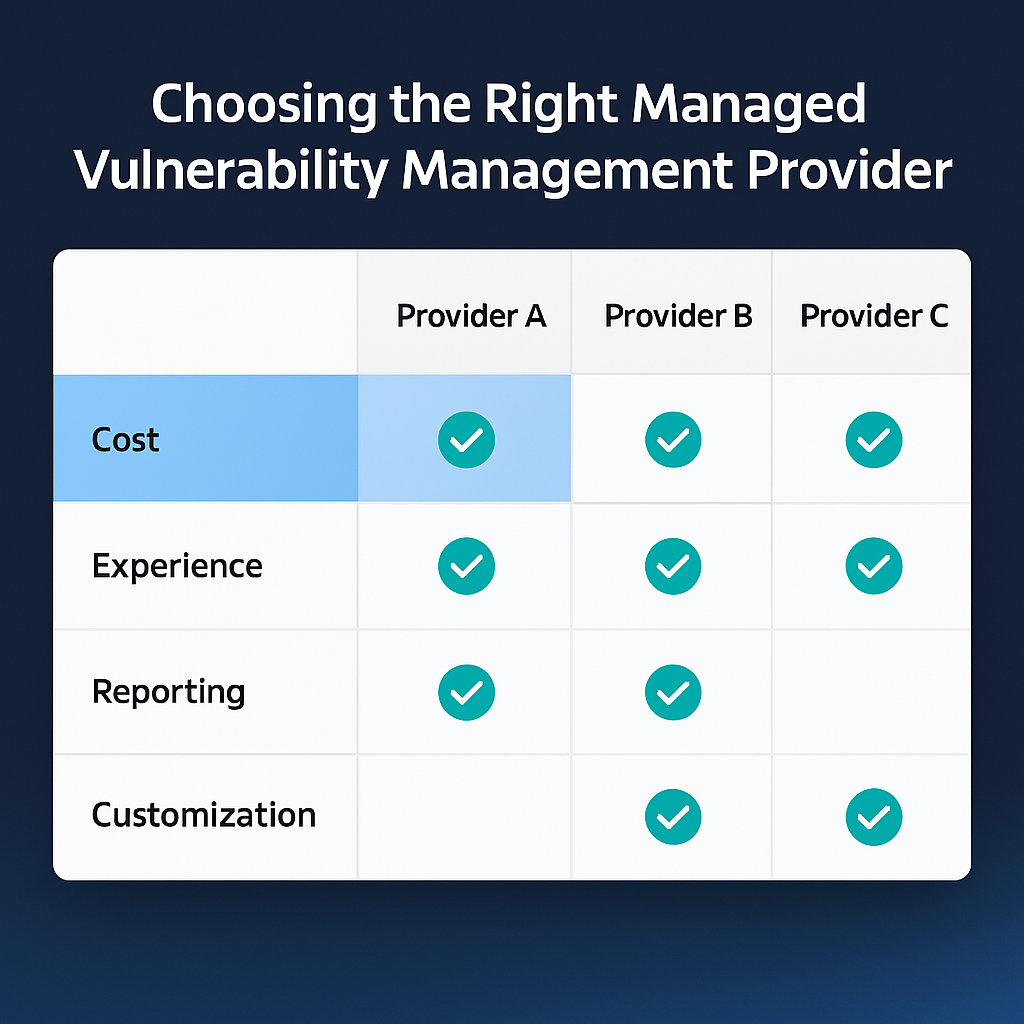
Choosing the right managed vulnerability management provider is key to your vulnerability management programme. When evaluating providers consider:
Managed vulnerability management services are cost effective because smaller teams don’t need in-house skills.
Providers like GuidePoint Security support various cybersecurity questions and challenges and stay relevant by evolving with the changing cybersecurity landscape. GuidePoint Security is a partner and advisor in cybersecurity so organisations get expert guidance and support in resolving vulnerabilities.
A strong partnership in managed vulnerability management requires:
Managed vulnerability management services provide continuous vulnerability scanning so organisations can identify threats in real-time. These services typically include ongoing scans that identify and prioritise vulnerabilities across an organisation’s assets. Compliance and audit support is often included to ensure adherence to relevant security regulations and standards.
A key capability of managed vulnerability management providers is the integration of threat intelligence to keep security up to date. Effective managed vulnerability management services include risk prioritisation frameworks such as CVSS to help clients focus on the most critical vulnerabilities first using a vulnerability management platform.
Many providers offer customisable engagement models so organisations can choose between fully outsourced services or a hybrid approach that includes internal management. Transparent reporting features are essential so clients can see vulnerability status, remediation efforts and overall security posture.
Reviewing customer testimonials is a critical step in choosing a managed vulnerability management provider. Testimonials give insight into a provider’s reliability and effectiveness in managing vulnerabilities and provide valuable information about their performance and customer satisfaction.
Considering other businesses experiences helps you make an informed decision and choose a provider that fits your organisation’s needs and expectations.
In summary managed vulnerability management services offer a comprehensive and proactive approach to identifying, prioritising and remediating vulnerabilities. By outsourcing this critical function organisations can benefit from cost efficiency, access to specialist knowledge and enhanced compliance and risk management. The managed vulnerability management lifecycle with its focus on continuous improvement and monitoring means organisations stay ahead of emerging threats and have a robust security posture.
Following best practices such as regular vulnerability scans, risk based remediation planning and continuous communication with security teams can further improve your vulnerability management programme. By choosing the right managed vulnerability management provider you can ensure your organisation gets the support and expertise to navigate the complex world of cybersecurity. Act now and secure your organisation’s future and stay ahead of cyber threats.
Managed vulnerability management lets you outsource the entire vulnerability lifecycle to third party providers so you can manage vulnerabilities without an in-house team. This simplifies the process and leverages external expertise.
Managed vulnerability management services means rapid response to security threats, ongoing monitoring and compliance support, and overall better security posture.
The key components of managed vulnerability management services are dynamic asset discovery, vulnerability scanning, ongoing monitoring and strategic remediation. Working with experts means comprehensive management and timely response to vulnerabilities.
Managed vulnerability management services helps with cost savings by letting you outsource this function so you don’t need an in-house team and internal resources can focus on core business objectives. Ultimately this means more cost effective solutions and operational savings.
Look for a managed vulnerability management provider that offers clear communication, proven expertise and flexible solutions that fit your needs. Also look for transparent reporting and alignment with your organisation’s security culture.
Schedule a consultation with us today and take the first step towards securing your digital future.